Troy Hunt (no relation, but a really great first name) has a post explaining “Collection #1” on his blog. Rarely do people read about online security because it can be complex and confusing. However, online security is crucial. In the case of identity theft, it general takes between 100 to 200 hours and six months to fix. While it isn’t fun to protect your identity, it sure beats the frustration involved in spending hundreds of hours to fix.
Troy’s information is powerful and useful. I suggest that you take a few minutes to read the post.
What follows is some basic information and advice.
Collection #1
Collection #1 is a database of almost 773 million unique email addresses (there are actually 2,692,818,238 rows of data – some are duplicates). This means that almost assuredly your email and password combination (at least one the you’ve used somewhere) are known by hackers.
Action
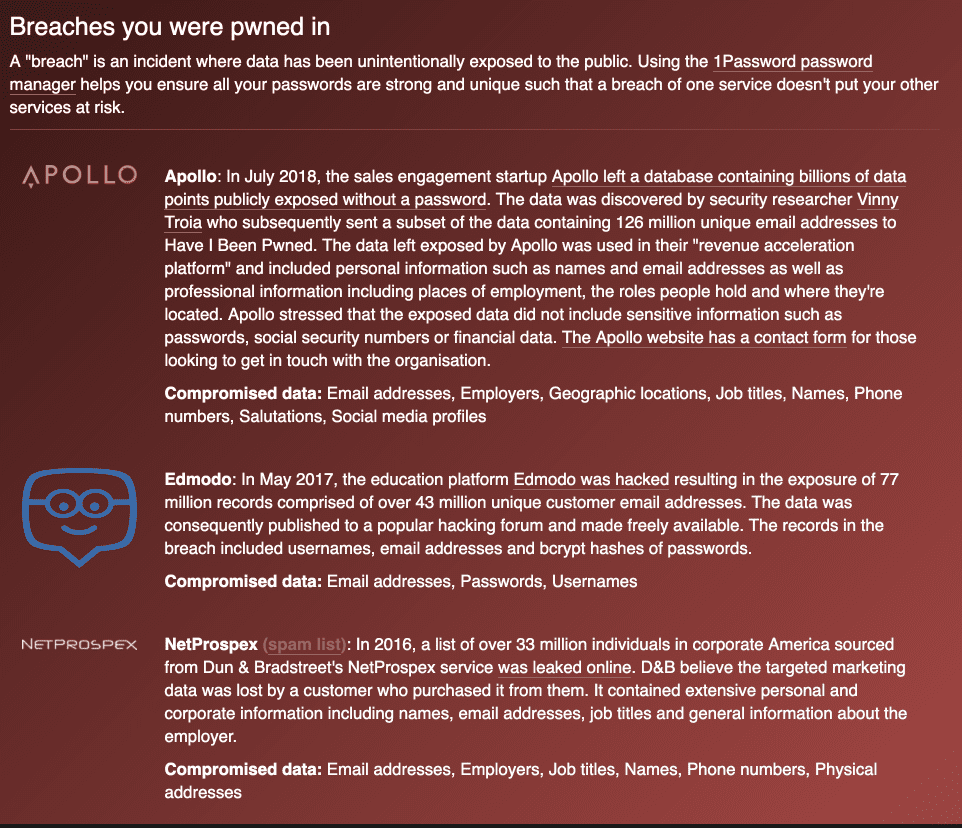
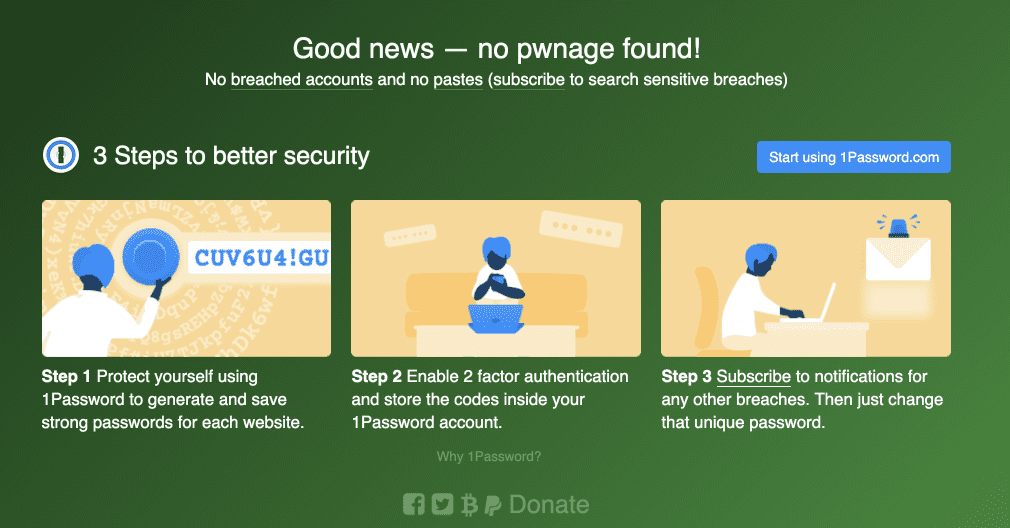
How do you know for sure if your email has been leaked? Head over to Have I Been Pwned. Enter your email address. Click on the “pwned?” button. I’ll share that a couple of my email addresses are available to hackers/spammers (some on sites that I’ve completely forgotten about/not sure I ever went there) and some aren’t. The results also include what was leaked. In some cases, the leaked information is demographic information; in other cases, user names and passwords were leaked. See the results below:
Email Address #1
Email Address #2
Credential Stuffing
So, how do hackers and spammers use this information? One way is credential stuffing. Essentially, they take the user names and passwords that have been leaked and try those on other sites. Since many people reuse passwords and email addresses, it is very likely that one combination will work in many places. Importantly, this doesn’t mean that you specifically were targeted, just that you were on the list. (Many people think that they are “safe” because they aren’t well known, aren’t especially “rich”, aren’t on a lot of sites, etc. Credential stuffing isn’t personal at all- to hackers. It become very personal for you if it works and you have to deal with the cleanup).
Next Steps
This is where I recommend to never reuse passphrases. In order to realistically do that, a Password Manager is a must. I’ve written about these before. Free options exist but are limited to a small number of devices. This is one of those things that I’m willing to pay for. (And I have. I purchased a family account of 1Password many, many years ago. 1Password has teamed up with Have I Been Pwned, but this isn’t a sales pitch for them. There are several good password managers available).
Most importantly, do not reuse the same password (passphrase) over and over.
Turn on 2 Step Authentication wherever possible. Although certainly not a cure-all, 2 Step Authentication can be a powerful assist in keeping you safe.