One of the things that we take very seriously is security. The safety and security of our users and data are important. This responsibility is not just for the Technology Department but is the responsibility of every user. Some times, people do what is expedient, instead of what is safe. One example that we had this year was a teacher signing into a computer and then letting a substitute use that computer. Unfortunately, the substitute made some poor decisions. (Just a reminder to NEVER share your credentials with someone else or sign into a computer and let someone else use it. This can lead to many uncomfortable situations. It’s also against federal law).
Because we take security seriously, we frequently have to ask questions and seek clarification about accounts and access. Recently, I had someone ask why I cared, and what were the possibilities of a compromise (frequently called a “hack”, but hacking is more specific than a compromise) of our data.
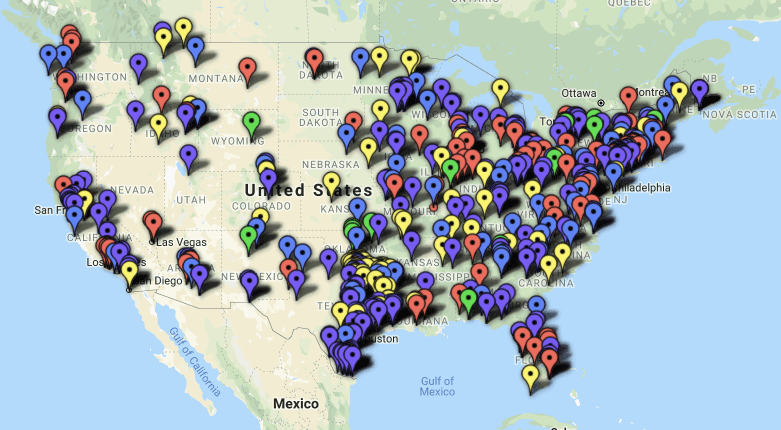
The K-12 Cybersecurity Resource Center posted a map of Cyber Incidents:
*Note that these are only the reported compromises.
Compromises occur due to a wide range of conditions that include, but are not limited to:
- a misconfiguration on a server
- an employee giving out their credentials
- a contractor who copies information
- malware installed by a user
- ransomware installed by a user
- email phishing that was successful
These compromises happen to all different sizes of districts and background. While the districts vary greatly in terms of size, socio-economic status, funding and more, the impact is similar for all.
…the impact of publicly-reported K-12 cyber incidents is significant. During 2018, such incidents resulted in the theft of millions of tax payer dollars, stolen identities, tax fraud, altered school records, website and social media defacement, and the loss of access to school technology and IT systems for weeks or longer.
Recently, several other governmental agencies have been successfully compromised. The cost of recovering from those compromises can be expensive in terms of actual dollars, time to recover and lost data.
- Baltimore – $18.2 million dollars
- Atlanta – $2.7 million dollars
- Riveria Beach – $600,000
These are only a few of the city governments that have been compromised. There are a great many more agencies and businesses that have been compromised.
We anticipate attempts to compromise networks to continue to increase. Importantly, one of the most important defenses against compromise is every user. There are important steps that you can take:
- NEVER share your passphrase with anyone
- Do not reuse passwords on multiple sites
- Be wise about making sure that you are not entering your user name and password on a scam site (you should be going to the site, not using a link)
- Turn on 2-step authentication everywhere that you can
- Report suspicious sites
Please bear this in mind the next time security questions come up. The Technology Department is being “mean” or “rude”, the stakes for online security are high.